After applying enrichment, a log can display additional information not initially collected. For example, consider a log indicating an unsuccessful authentication attempt by user Alice in the sales portal. Initially, the log contains only Alice’s username and the login timestamp. By configuring an enrichment source, additional details such as her department and email are fetched and added to the log. This allows a security analyst to verify whether Alice belongs to the authorized user group.
The second of the following two screenshots shows what an enriched log looks like compared to an unenriched one.
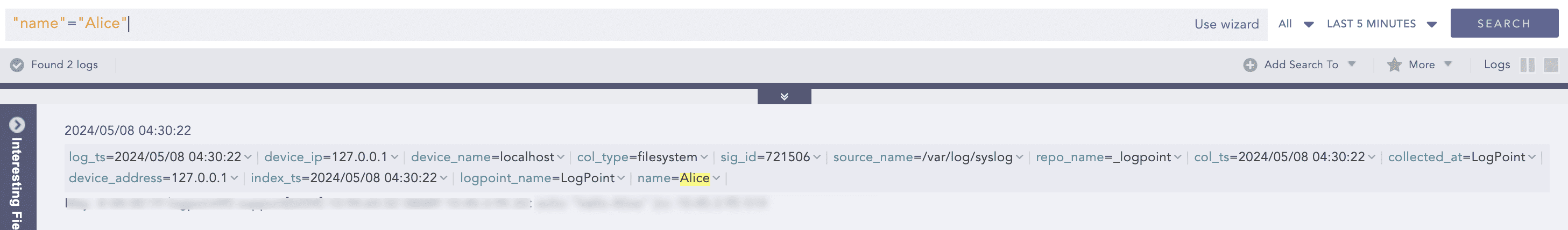
Unenriched Log Sample¶
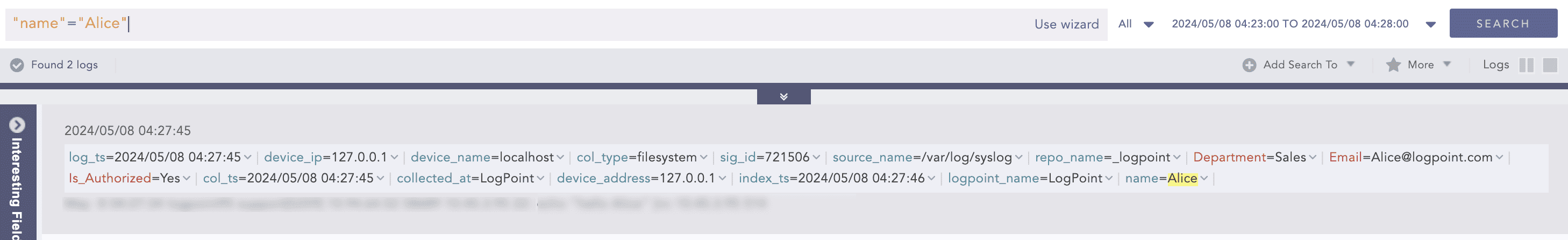
Enriched Log Sample¶
We are glad this guide helped.
Please don't include any personal information in your comment
Contact Support